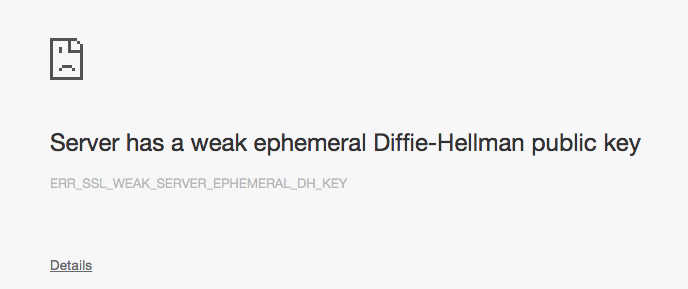
I ran into this short stopper today, which prevented access to the Admin interfaces of my Solr indexer:
ERR_SSL_WEAK_SERVER_EPHEMERAL_DH_KEY
Recalling how difficult it was to first enable SSL with my Solr cluster.. I suspected this would be a major issue (and for the most part it was)
STACK OVERFLOW TO THE RESCUE!
Using this article: How to fix ERR_SSL_WEAK_SERVER_EPHEMERAL_DH_KEY I was able to modify my Solr 5 / Jetty configuration to stop use of the weaker DH keys.
The first solution using the wildcarded names did not work for me. After a couple of hours of testing and looking at my logs, I found that another un-voted solution fixed the issue without much hassle.
The Fix
The configuration file I modified to resolve this is the jetty-https-ssl.xml. It is located in /opt/solr/server/etc on my server.. your situation might be a little different (you’ll need to find that file that is in use by Solr yourself if it’s not in the above location).
[root@]cd /opt/solr/server/etc
[root@]vi jetty-https-ssl.xml
Locate the block where you have your SSL config. This is what mine looks like:
<Call name=”addConnector”>
<Arg>
<New class=”org.eclipse.jetty.server.ssl.SslSelectChannelConnector”>
<Arg>
<New class=”org.eclipse.jetty.http.ssl.SslContextFactory”><Set name=”keyStore”><SystemProperty name=”jetty.home” default=”.”/>/etc/solr-ssl.keystore.jks</Set>
<Set name=”keyStorePassword”>9290j2039fh09209h390h8f23</Set>
<Set name=”needClientAuth”><SystemProperty name=”jetty.ssl.clientAuth” default=”false”/></Set></New>
</Arg><Set name=”port”><SystemProperty name=”jetty.ssl.port” default=”8984″/></Set>
<Set name=”maxIdleTime”>30000</Set>
</New>
</Arg>
</Call>
Within the NEW block, below existing values.. I added this complete section, verbatim:
<!– //START ADDED 9-SEP-2015 for Diffie-Hellman group size Fix –><Set name=”ExcludeCipherSuites”>
<Array type=”String”>
<Item>SSL_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_RSA_WITH_DES_CBC_SHA</Item>
<Item>SSL_DHE_DSS_WITH_DES_CBC_SHA</Item>
<Item>SSL_RSA_EXPORT_WITH_RC4_40_MD5</Item>
<Item>SSL_RSA_EXPORT_WITH_DES40_CBC_SHA</Item>
<Item>SSL_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA</Item>
<!– Disable small Diffie-Hellman key exchange to prevent Logjam attack —>
<Item>SSL_DHE_RSA_WITH_3DES_EDE_CBC_SHA</Item>
<Item>SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA</Item>
<Item>TLS_DHE_RSA_WITH_AES_256_CBC_SHA256</Item>
<Item>TLS_DHE_DSS_WITH_AES_256_CBC_SHA256</Item>
<Item>TLS_DHE_RSA_WITH_AES_256_CBC_SHA</Item>
<Item>TLS_DHE_DSS_WITH_AES_256_CBC_SHA</Item>
<Item>TLS_DHE_RSA_WITH_AES_128_CBC_SHA256</Item>
<Item>TLS_DHE_DSS_WITH_AES_128_CBC_SHA256</Item>
<Item>TLS_DHE_RSA_WITH_AES_128_CBC_SHA</Item>
<Item>TLS_DHE_DSS_WITH_AES_128_CBC_SHA</Item>
</Array>
</Set><Set name=”ExcludeProtocols”>
<Array type=”java.lang.String”>
<Item>SSLv3</Item>
</Array>
</Set><!– //END Diffie-Hellman group size Fix –>
Once that was added, I saved the file and I restarted solr:
[root@]cd /opt/solr/server/etc
Sending stop command to Solr running on port 8984 … waiting 5 seconds to allow Jetty process 3861 to stop gracefully.
Waiting to see Solr listening on port 8984 [-]
Started Solr server on port 8984 (pid=4162). Happy searching!
Re-trying my Solr Admin… BACK IN BUSINESS!!! 😀